|
Virtual Private Networks (VPN) |
|
Communication Consultants |
|
Paul Colmer & Associates |





|
Home |
|
About Us |
|
Open Source |
|
Service List |
|
Consulting |
|
VOIP |
|
Network Design |
|
WAN |
|
VPN |
|
LAN |
|
WLAN |
|
Hub & Spoke vs Mesh |
|
Undersea Fiber |
|
IT Support |
|
Training |
|
Web Design |
|
Product List |
|
Case studies |
|
News Article |
|
Contact Us |
|
About Us |
|
Home |
|
Recruitment services |
|
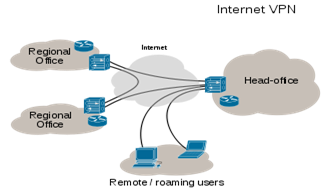
Paul Colmer & Associates are able to design and implement VPN networks both locally and internationally to provide the bandwidth and security that each individual client requires. A virtual private network (VPN) is a computer network that is constructed by using public networks or wires such as Internet to provide remote offices or individual users to get secure access to their organization's network. This network uses encryption and other security mechanisms to ensure that only authorised users be able to participate in the communications and that the data cannot be intercepted. It aims to avoid an expensive system of privately owned or leased lines that can be used by only one organization. The use of a public network, usually the Internet, to connect securely to a private network, is the basis of a VPN. Companies and organizations will use a VPN to communicate confidentially over a public network; the VPN can be used to send voice, video or data. It is an excellent option for remote workers and organizations with global offices and partners to share data in private manner. It encapsulates data transfers using a secure cryptographic method between two or more networked devices which are not on the same private network so as to keep the transferred data private from other devices on one or more intervening local or wide area networks. There are many different classifications, implementations, and uses for VPNs. Trusted delivery networks
On the other hand provider-provided VPNs (PPVPNs) need to support coexisting multiple VPNs, Trusted VPNs do not use cryptographic tunnelling, and instead rely on the security of a single provider's network to protect the traffic. Multi-Protocol Label Switching (MPLS) is often used to overlay VPNs, often with quality-of-service control over a trusted delivery network. Layer 2 Tunnelling Protocol (L2TP) which is a standards-based replacement, and a compromise taking the good features from each, for two proprietary VPN protocols: Cisco's Layer 2 Forwarding (L2F)(obsolete as of 2009) and Microsoft's Point-to-Point Tunnelling Protocol (PPTP). From the security standpoint, VPNs either trust the underlying delivery network, or must enforce security with mechanisms in the VPN itself. Unless the trusted delivery network runs among physically secure sites only, both trusted and secure models need an authentication mechanism for users to gain access to the VPN. VPNs in mobile environments
Mobile VPNs are used in a setting where an endpoint of the VPN is not fixed to a single IP address, but instead roams across various networks such as data networks from cellular carriers or between multiple Wi-Fi access points. Mobile VPNs have been widely used in public safety, where they give law enforcement officers access to mission-critical applications, such as computer-assisted dispatch and criminal databases, as they travel between different subnets of a mobile network. They are also used in field service management and by healthcare organizations, among other industries. Increasingly, mobile VPNs are being adopted by mobile professionals and white-collar workers who need reliable connections. They allow users to roam seamlessly across networks and in and out of wireless-coverage areas without losing application sessions or dropping the secure VPN session. A conventional VPN cannot survive such events because the network tunnel is disrupted, causing applications to disconnect, time out, or fail, or even cause the computing device itself to crash. Instead of logically tying the endpoint of the network tunnel to the physical IP address, each tunnel is bound to a permanently associated IP address at the device. The mobile VPN software handles the necessary network authentication and maintains the network sessions in a manner transparent to the application and the user. The Host Identity Protocol (HIP), under study by the Internet Engineering Task Force, is designed to support mobility of hosts by separating the role of IP addresses for host identification from their locator functionality in an IP network. With HIP a mobile host maintains its logical connections established via the host identity identifier while associating with different IP addresses when roaming between access networks. from one another, but operated by the same service provider. |
|
Tunnelling protocols can be used in a point-to-point topology that would theoretically not be considered a VPN, because a VPN by definition is expected to support arbitrary and changing sets of network nodes. But since most router implementations support a software-defined tunnel interface, customer-provisioned VPNs often are simply defined tunnels running conventional routing protocols. |